NXaaS in Action: CAMARA Security APIs serve Financial Services
How Network-Level Intelligence Stops Fraud Before It Happens
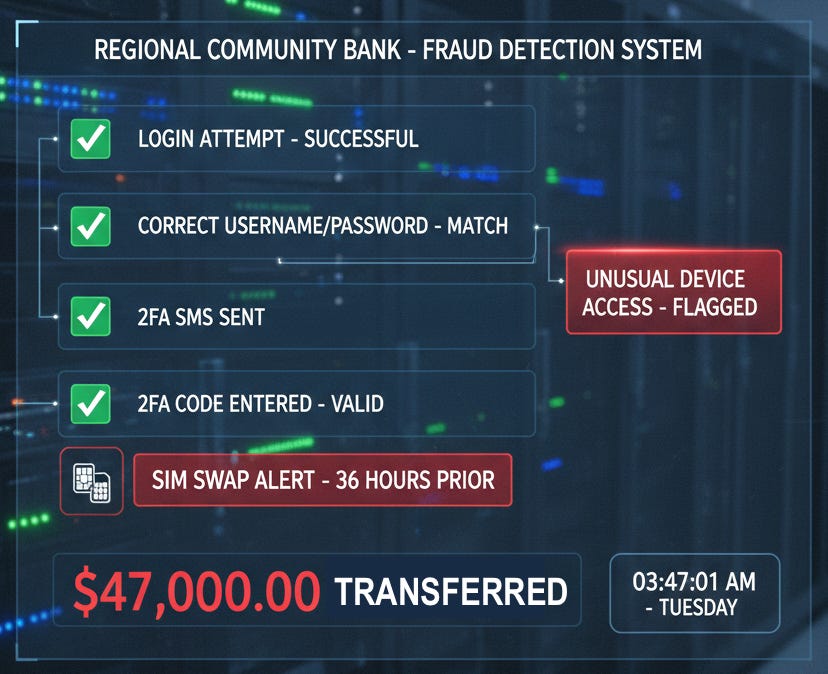
At 3:47 AM on a Tuesday morning, the fraud detection system at Regional Community Bank flagged an unusual login attempt. A customer was accessing their account from a device that appeared legitimate, using the correct username and password. The system sent a two-factor authentication code via SMS. Within seconds, someone entered the correct code.
Everything looked normal. But it wasn’t.
What the bank’s traditional security systems couldn’t see was that the customer’s phone number had been transferred to a different SIM card just 36 hours earlier—a telltale sign of SIM swap fraud. By the time the bank’s team discovered the breach during their morning review, $47,000 had been transferred out of the customer’s account.
This scenario plays out hundreds of times every day across financial institutions. Fraudsters have learned to exploit the gap between what authentication systems can see (passwords, codes, device identifiers) and what they can’t see (network-level signals that indicate whether a device and connection are genuinely trustworthy).
But there’s a fundamental problem: the most powerful security signals—the ones that mobile carriers use to protect billions of users worldwide—have been locked away inside telecom networks, inaccessible to the organizations that need them most.
Until now.
The CAMARA Revolution: Opening Network Intelligence
CAMARA is a global open-source initiative that standardizes access to telecom network capabilities through APIs. Think of it as unlocking the security vault that carriers have been using for decades and making those capabilities available to any organization that needs to verify trust at the network level.
For financial institutions, this represents a paradigm shift. Instead of relying solely on passwords, security questions, and SMS codes—all of which can be compromised—banks can now query the mobile network itself to verify whether a user’s device and connection are genuine, active, and safe.
The Security Gap That Banks Face
Traditional authentication systems operate with critical blind spots:
What they can verify:
Username and password match
Security question answers are correct
SMS code was entered accurately
Device fingerprint looks familiar
IP address appears reasonable
What they cannot see:
Whether the phone number was hijacked yesterday
If the SIM card is the same one the customer has been using
Whether the device itself was recently swapped
If the user is genuinely at the location they claim
Whether the mobile connection is coming from the legitimate carrier
These blind spots create the vulnerabilities that fraudsters exploit. SIM swap fraud, where criminals convince mobile carriers to transfer a victim’s phone number to a SIM card they control, is a leading cause of account takeover attacks. Once they have control of the phone number, they can intercept SMS authentication codes, reset passwords, and drain accounts—all while appearing to use legitimate credentials.
This is where CAMARA APIs, integrated through NXaaS, transform security from reactive to proactive.
NXaaS + CAMARA: Network-Level Security for Banks
Bug Labs’ NXaaS platform integrates CAMARA security APIs to provide financial institutions with real-time, network-level fraud prevention—without the complexity of managing multiple carrier relationships or navigating different API implementations across regions.
Here’s how it works in practice:
SIM Swap Detection: Stopping Fraud Before It Happens
The SIM Swap API monitors and detects changes in the SIM card associated with a mobile number, providing banks with insights into whether a SIM card has been swapped recently or offering real-time notifications when a SIM card status changes.
When a customer attempts to log in, transfer funds, or access sensitive data, the system queries the SIM Swap API through NXaaS:
Query: “Has the SIM card associated with phone number +1-555-0123 been swapped in the last 72 hours?”
Response: “Yes. SIM swap detected 38 hours ago.”
Action: Instead of sending an SMS code that would go to the fraudster’s device, the system triggers additional verification steps: biometric authentication, a call to the customer’s registered backup number, or a temporary account freeze with email notification.
The customer experiences a minor inconvenience—an extra verification step—but their account remains secure. The fraudster is blocked before they can cause damage.
Number Verification: Invisible Authentication
The Number Verification API leverages mobile network mechanisms to confirm that the phone number provided matches the one associated with the user’s device, eliminating the need for SMS codes and reducing risks from phishing, SIM swapping, and account takeover attacks.
This creates “silent authentication”—the customer doesn’t need to enter a code, wait for a text, or take any action. The network itself confirms their identity in milliseconds:
Customer attempts to log in from their mobile device
Application sends verification request through NXaaS/CAMARA
Mobile network confirms the device is legitimately associated with that phone number
Customer is authenticated and granted access
This transparent operation ensures customers enjoy a smooth experience without interruptions, leading to higher conversion rates and reduced abandonment during critical transactions.
Device Swap Detection: Identifying Suspicious Changes
The Device Swap API enables banks to detect when the physical device associated with a phone number has been recently changed, another indicator of potential account takeover attempts. When combined with SIM Swap detection, this provides a comprehensive view of whether a mobile connection is genuinely trustworthy.
Real-World Case Study: Regional Community Bank
Let’s return to that 3:47 AM login attempt. With NXaaS-integrated CAMARA APIs, here’s what actually happens:
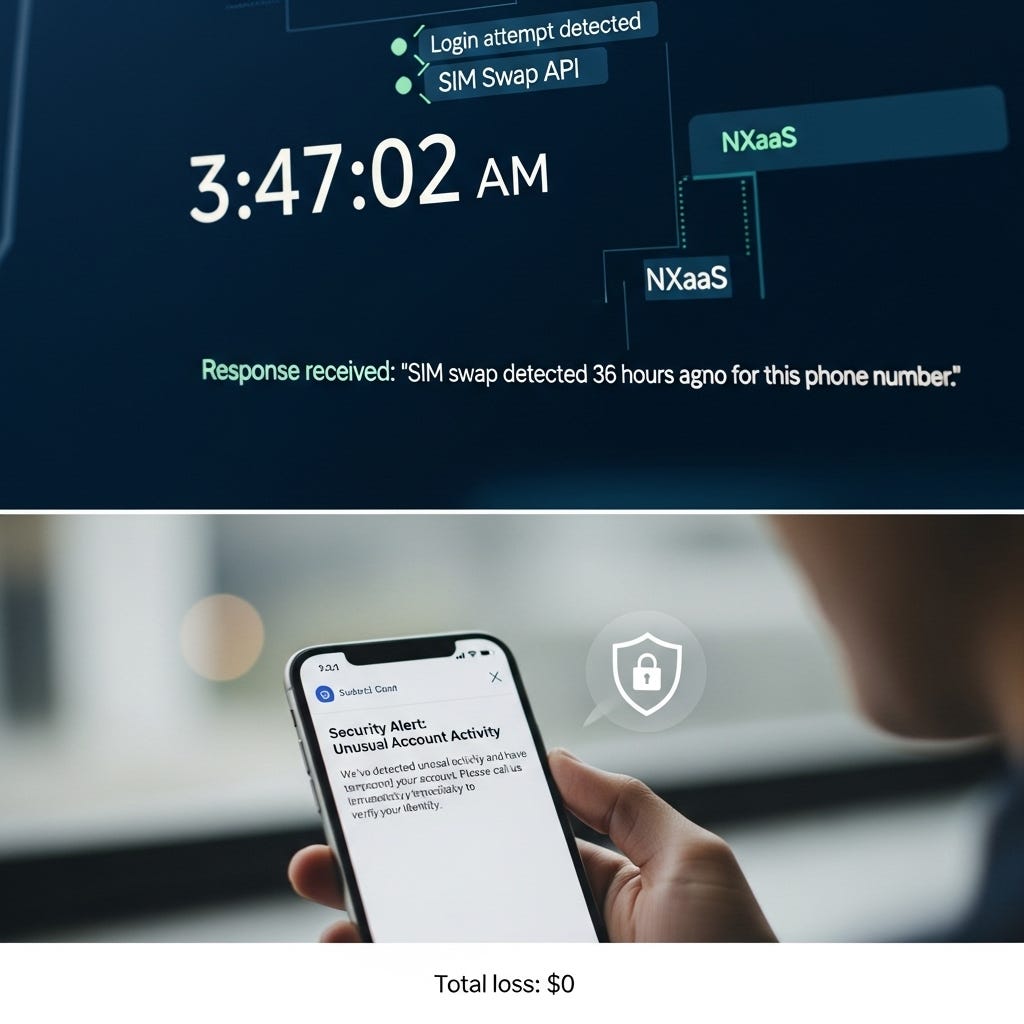
3:47:02 AM - Login attempt detected. System queries SIM Swap API through NXaaS.
3:47:03 AM - Response received: “SIM swap detected 36 hours ago for this phone number.”
3:47:04 AM - Instead of sending SMS code, system triggers high-risk authentication protocol:
Temporary transaction freeze
Email sent to registered address: “We’ve detected unusual activity and have temporarily secured your account. Please call us immediately at [number] to verify your identity.”
Alert sent to fraud prevention team
3:47:15 AM - Fraudster, unable to proceed, abandons attempt.
8:23 AM - Legitimate customer checks email, sees security alert, calls bank.
8:35 AM - Bank confirms SIM swap was unauthorized, helps customer secure their mobile account, unlocks banking access with new verification protocols.
Total Loss: $0
Customer impact: Minor inconvenience, but account and funds protected.
Alternative scenario without CAMARA: $47,000 loss, weeks of fraud investigation, potential unrecoverable funds, damaged customer trust.
The Business Case: Security That Pays for Itself
Let’s quantify the impact with conservative estimates for a mid-sized regional bank with 500,000 customers:
Traditional Security Costs (Annual):
Account takeover fraud losses: $8-12 million
Fraud investigation and remediation: $2.5 million
Customer support for fraud victims: $1.8 million
Regulatory fines and legal costs from breaches: $500,000-3 million
Reputational damage and customer churn: difficult to quantify, but significant
Total: $12.8-19.3 million annually
With NXaaS/CAMARA Security APIs:
API transaction costs: $350,000 annually (assuming verification on 40% of logins and transactions)
Integration and maintenance: $200,000 first year, $50,000 ongoing
Reduced fraud losses (70% reduction): $2.4-3.6 million
Reduced investigation costs (60% reduction): $1 million
Reduced support costs (50% reduction): $900,000
Reduced regulatory exposure (80% reduction): $100,000-600,000
Total costs: $4.4-5.55 million annually
Net annual savings: $7.25-13.75 million
ROI: 1,260% to 2,390%
And this doesn’t account for:
Prevented reputational damage
Improved customer trust and retention
Reduced insurance premiums for cyber liability coverage
Competitive advantage from superior security posture
The Multi-Region Challenge
For banks operating internationally, the complexity multiplies exponentially. Each country has different dominant carriers, different regulatory requirements, and different CAMARA implementation timelines.
NXaaS handles this complexity behind a single interface. Whether your customer is using Vodafone in Germany, Orange in France, or Reliance Jio in India, your application makes the same API call. NXaaS routes the request to the appropriate carrier and returns a standardized response.
The Invisible Security Layer
Perhaps the most important benefit of CAMARA APIs through NXaaS is that they create security that’s invisible to legitimate customers while being impenetrable to fraudsters.
Consider the traditional security trade-off: more security means more friction. Make customers answer security questions, enter longer passwords, complete CAPTCHAs, wait for email confirmations, and you’ve made systems more secure—but also more annoying. Customers abandon transactions, call support lines, or find workarounds that undermine your security.
CAMARA APIs break this trade-off. When verification happens at the network level:
Legitimate customers experience zero additional steps
Authentication is faster, not slower (no waiting for SMS codes)
Security is stronger because it’s based on network-level signals that fraudsters can’t manipulate
Fraud prevention is proactive rather than reactive
The customer logging in from their usual device sees instant authentication. The fraudster attempting to use a compromised SIM card is blocked before they can do damage. Same API call, dramatically different outcomes based on actual network-level trustworthiness.
The Path to Implementation
Banks ready to integrate CAMARA security APIs through NXaaS typically follow this path:
Phase 1: Risk Assessment (1-2 weeks)
Identify high-risk authentication and transaction scenarios
Determine which CAMARA APIs provide the most value
Establish baseline fraud metrics for ROI measurement
Phase 2: Pilot Implementation (4-8 weeks)
Deploy CAMARA APIs for specific use case (often SIM Swap detection for high-value transactions)
Run in monitoring mode alongside existing security systems
Validate detection accuracy and measure impact on fraud attempts
Phase 3: Progressive Rollout (8-16 weeks)
Expand to additional use cases and customer segments
Implement automated response protocols
Integrate with fraud prevention and risk management systems
Train security and support teams on new capabilities
Phase 4: Optimization and Expansion (Ongoing)
Refine risk thresholds based on operational data
Add new CAMARA APIs as they become available
Expand to additional regions or business units
Continuously improve ROI through usage optimization
Because NXaaS handles the carrier complexity, banks can move quickly through these phases. The typical time from decision to production deployment is 3-6 months—not years.
Conclusion: Turning the Network Into Your Fraud Prevention Layer
Account takeover fraud, SIM swap attacks, and authentication compromises are growing more sophisticated every day. Traditional security approaches are necessary but no longer sufficient.
The mobile network has always been one of the world’s most sophisticated security infrastructures. With CAMARA and NXaaS, that power is finally available to financial institutions that need it most.
By integrating CAMARA security APIs and delivering them through a unified platform, Bug Labs makes network-level fraud prevention accessible to any bank, credit union, fintech, or financial services provider that needs to protect customer accounts and assets.
Invisible to customers. Impenetrable to fraudsters. Integrated in months, not years.
That’s network-level security as a service.
Ready to protect your financial institution with network-level security intelligence? Contact Bug Labs to learn how NXaaS-integrated CAMARA APIs can transform your fraud prevention and authentication systems—without the complexity of direct carrier integration.